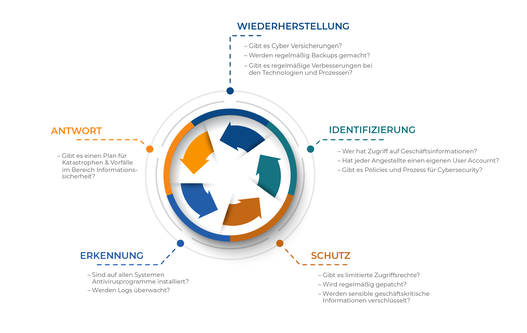
- What IT security strategy does an organization pursue?
- Which standards and norms does the company/agency follow when deriving measures to improve cybersecurity?
- How effective are controls already in place? Which controls are still missing?
- Which roles are defined in the area of IT security and which binding documents regulate their cooperation?
- Which technical solutions are used to detect and prevent digital attacks?
Make effective risk management with IT security frameworks
Vulnerabilities in IT easily become a gateway for hackers. And the digitalization of business processes and stronger technical networking with customers and suppliers ultimately increase the organization's attack surface. To keep pace with these developments and derive suitable protective measures, methodical standards are needed, e.g. ISO/IEC 2700X.
We are your partner for deriving, implementing and testing an IT security framework.
We support the selection and implementation of an IT security framework
As external IT auditors, we have helped numerous organizations audit their IT infrastructure, assess identified organizational and technical vulnerabilities, and derive and implement holistic cybersecurity frameworks.
Cybersecurity Framework Design
Cybersecurity Framework Implementation
Cybersecurity Audit
End Of Life Monitoring

We are ISO certified:
TIMETOACT Software & Consulting GmbH has successfully implemented an ISMS and received ISO 27001 certification. With our ISMS, TIMETOACT creates a high level of IT security according to international standards and thus officially stands for information security.
Benefit from a professional IT Security:
Risk Management
Vulnerability analysis
Better Practices
Effectiveness control
What is IT security?
IT security includes organizational and technical protective measures to protect IT (computers, mobile devices, server systems, software, data, networks, data centers) against cyber attacks. Identifying the appropriate measures in each case and implementing them effectively is a Herculean task. Cybersecurity frameworks offer orientation in all this complexity. These are a set of published rules and better practices designed to strengthen the resilience of enterprises and government agencies against cyberattacks.
What is an Information Security Management System (ISMS)?
An Information Security Management System (ISMS) is an overview of the company's methods, guidelines and rules. This overview helps the security experts to reduce the risks for the company. An information security management system is already mandatory for critical infrastructures, but companies from other sectors are now also adapting to the increased risk of cyberattacks.
The ISMS clearly defines responsibilities and tasks as well as how to deal with risks. It thus provides companies with a guideline for cybersecurity.
We can help you implement an effective and efficient ISMS through our experience.
Our approach
With these steps we support you in the implementation of IT security:
- Recording of the existing IT security strategy
- Review of the suitability of the implemented IT security framework for achieving the strategic objectives
Derivation of an adapted IT security framework (better practices) including:
- Guiding principles (risk management, prevention before intervention, data protection, etc.)
- Governance (roles, responsibilities), Processes (Identify, Protect, Discover, Respond, Recover)
- Tools
- Developing a roadmap for the implementation of the IT Security Framework
- Ensure the implementation (in quality) of the IT Security Framework on time, on budget and aligned with the defined objectives
Regularly test the effectiveness of IT security controls:
- Collect evidence (policies, process documentation, reports, system logs) on the effectiveness of controls.
- Assess the maturity or completeness of security controls in the selected cybersecurity framework
- Document identified deviations
- Provide recommendations for improving controls
Feel free to contact us!

Digital transformation in public administration

Internal and external security

IT Service Management – Optimal support for IT processes

Enterprise Architecture – Synchronising Business and IT

Expedition zum Identity Management

IT Asset Management – Reducing Costs and Risks Sustainably

Security, Identity & Access Management

Demand Management – Clarity on IT needs

Application Development

Mix of IASP & ILMT support for optimal license management

IT Sourcing & Vendor Management – Managing IT Partners

IT strategy – A clear goal and the way to achieve it

IT Controlling – Determination and allocation of IT costs

Christof Mandaus

Application Modernization
HCL

FinOps Microsoft - Microsoft Cloud Cost Optimization
HCL

IPG Information Process Group Holding AG

Anwendungsmöglichkeiten

FinOps

Standardize and optimize project management | Atlassian

Cloud Migration | Atlassian

Digitization of the energy industry

License and software consulting from a single source

Introduction of Jira to Hamburger Hochbahn
Stefan Krax

Volker Jürgensen

Proof-of-Value Workshop

HCL Digital Xperience
Jira Service Management from Atlassian

Anton Peter

Cloud from Atlassian

FinOps Consulting

Consulting for IBM products

Data Governance

Enterprise Service Management
Data Science, Artificial Intelligence and Machine Learning

Dashboards & Reports

Business Intelligence

Data Integration, ETL and Data Virtualization

Conception of individual Analytics and Big Data solutions

Consulting for IBM products

Consulting for IBM products

TIMETOACT implements integrated insurance software

Consulting and solutions for AWS services

Consulting for IBM products

Consulting for IBM products

Consulting for IBM products

Consulting for IBM products

IBM Spectrum Protect

Talend migration in record time

Consulting for IBM products

On-site digitization partner for insurance companies

Big Data, Data Lake & Data Warehousing

Application Integration & Process Automation

Process Integration & Automation

Release change of a deployed IAM tool

Enterprise Content Management (ECM) & Archiving

Managed Services & Support

Agile Software Development

Enterprise Content Management (ECM) & Archiving

Insurance

Turck Holding Optimizes IT Structure

Efficient fleet management due to scalable platform

Benjamin Hering

Incident communication management

Modern and user-friendly service portal

IT-Service-Management (ITSM)

Hamid Ardouz

Reduce your costs with Software Asset Management (SAM)!

Process Transformation, Integration & Automation

Open Source Technologies
Data Vault Modeling Approach

Sascha Wadenpohl

Demand Planning, Forecasting and Optimization

Atlassian Crowd

Digitized processes increase efficiency
Confluence from Atlassian

Database technologies

Microsoft

Enterprise Application Integration

IT modernization and strategy

Software Asset Management

Onboarding solution of TIMETOACT

Bamboo, Bitbucket, Sourcetree

Requirement Engineering

IBM Cloud Pak for Data

Advice around Mendix

Security, Identity & Access Governance

TIMETOACT provides support for ISO/IEC 19770-1 certification

Digital Architecture

Workspace Security Assessment

Standardized data management creates basis for reporting

Architecture consulting

AI & Digitization for the Transportation and Logistics Indus

Open and secure IT

Digitalization and cloud transformation

Intelligent Document Processing (IDP)







